Authenticating Huddo Boards Cloud with HCL Connections¶
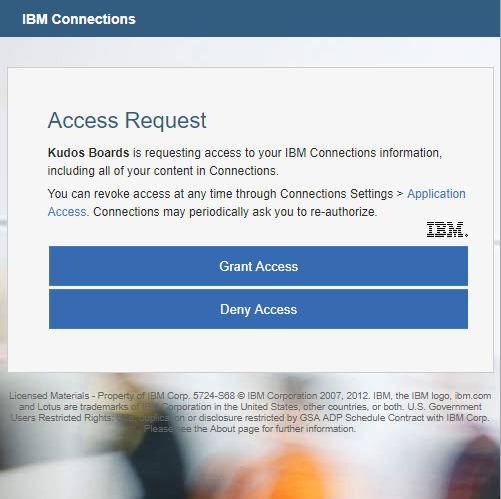
Register OAuth¶
In order for Huddo Boards to authenticate with your Connections environment, you must define a new OAuth widget.
-
SSH to the HCL Connections Deployment Manager (substitute the alias)
ssh root@[DEPLOY_MANAGER_ALIAS] -
Start
wsadmin(substitute your credentials)cd /opt/IBM/WebSphere/AppServer/profiles/Dmgr01/bin/ ./wsadmin.sh -lang jython -username connectionsadmin -password passw0rd -
Register the new application definition
execfile('oauthAdmin.py') OAuthApplicationRegistrationService.addApplication('huddoboards', 'Huddo Boards', 'https://boards.huddo.com/auth/connections/[CONNECTIONS_HOSTNAME_BASE64]/callback')Where
[CONNECTIONS_HOSTNAME_BASE64]is- your Connections hostname base64 encoded. E.g.
connections.example.com=>Y29ubmVjdGlvbnMuZXhhbXBsZS5jb20=There are many free online services to do this, ie here
- your Connections hostname base64 encoded. E.g.
-
To view the uniquely created client clientSecret
OAuthApplicationRegistrationService.getApplicationById('huddoboards')These commands will print the definition. Please take note of the
clientSecret. We will use this later on asCONNECTIONS_URL=https://connections.example.com CONNECTIONS_CLIENT_ID=huddoboards CONNECTIONS_CLIENT_SECRET=[VALUE_PRINTED]
Configure Auto Auth¶
Steps to configure the Huddo Boards application for auto-authorize (also documented here)
Tip
this step is optional but recommended and can be done at any time.
-
Add the new line to the following section in
[cellname]/oauth20/connectionsProvider.xmlNote: keep any existing values and add the new line for
huddoboards<parameter name="oauth20.autoauthorize.clients" type="ws" customizable="true"> <value>huddoboards</value> </parameter> -
Recreate the provider via this command:
Note: update the wsadmin credentials and the
[PATH_TO_CONFIG_FILE]./wsadmin.sh -lang jython -conntype SOAP -c "print AdminTask.createOAuthProvider('[-providerName connectionsProvider -fileName [PATH_TO_CONFIG_FILE]/oauth20/connectionsProvider.xml]')" -user connectionsadmin -password passw0rd -
Restart the WebSphere servers